Ingress Controller 部署
- Ingress 全局负载均衡,7层负载均衡(域名url), nodeport只支持4层(端口)
- 用户 -> Ingress Controller(Node) -> Pod
- 他会使用宿主机网络的 80和443端口,要确保node这俩个端口不要被占用
1 | 1. 通过service相关联 |
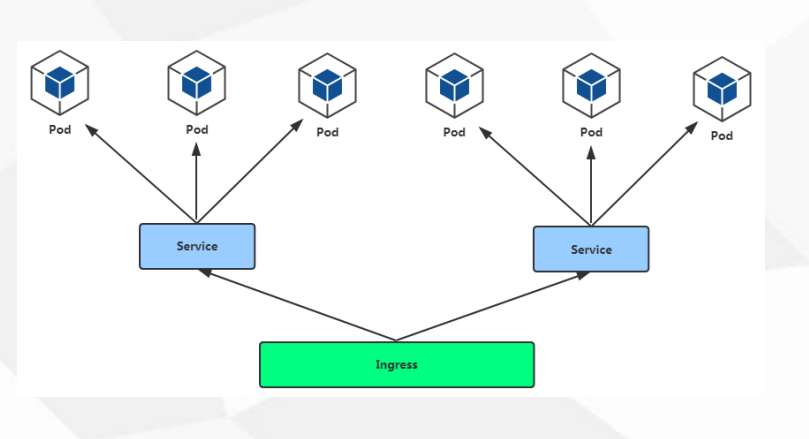
部署
1 | 部署文档: |
1 | 注意事项: |
1 | kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/static/mandatory.yaml |
1 | [root@k8s-master demo2]# kubectl create -f mandatory.yaml |
[root@k8s-master1 ~]# kubectl get pods -n ingress-nginx
NAME READY STATUS RESTARTS AGE
nginx-ingress-controller-8nbng 1/1 Running 12 6d8h
nginx-ingress-controller-dksf2 1/1 Running 10 6d8h
nginx-ingress-controller-rp5t2 1/1 Running 0 2m32s
1 | [root@k8s-node1 ~]# netstat -antp|grep 80 |
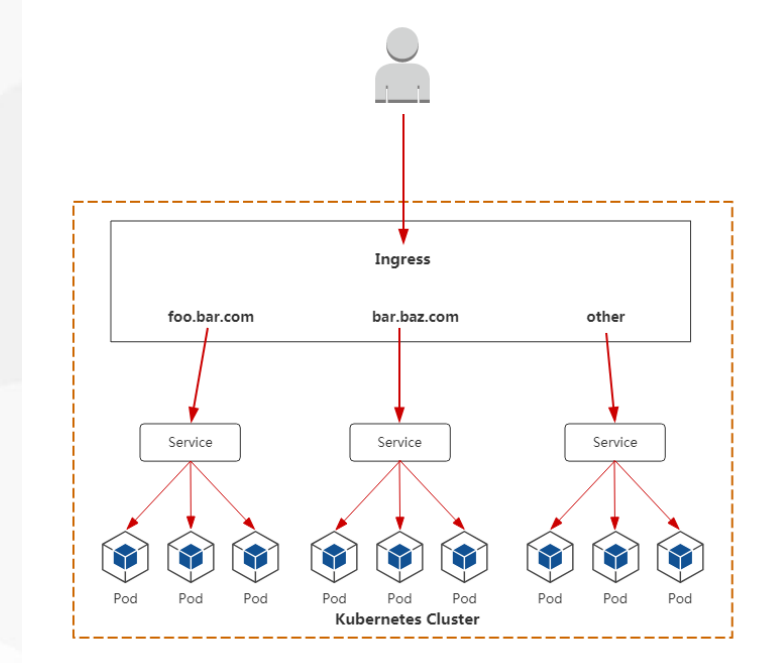
Ingress 配置
1 | [root@k8s-master1 demo]# vim app01-ingress.yaml |
1 | [root@k8s-master demo2]# kubectl apply -f ingress01.yaml |
1 | # 测试增加域名解析 |
深入的去看看 ingress-nginx
1 | [root@k8s-master1 demo]# kubectl get pods -n ingress-nginx -o wide |
Ingress HTTPS
- 域名 -> service 端口 -> pod
- https 需要定义 tls数字证书
- https 需要启动 crt和key
- 权威结构购买数字域名证书
- 自签证书 不受浏览器信任
- 证书保存到 secret里面 然后保存到 secretName下
自签证书 并 引用
1 | # 1. 生成证书 |
1 | # 保存到 secret |
1 | # 创建 ingress |
1 | # 启动 ingress-https |
1 | # 测试 |
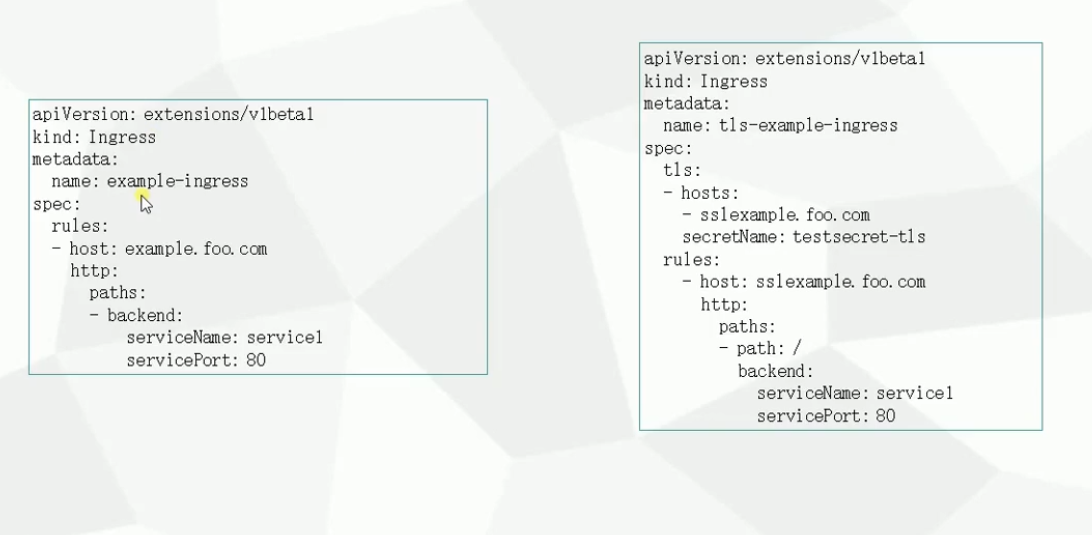
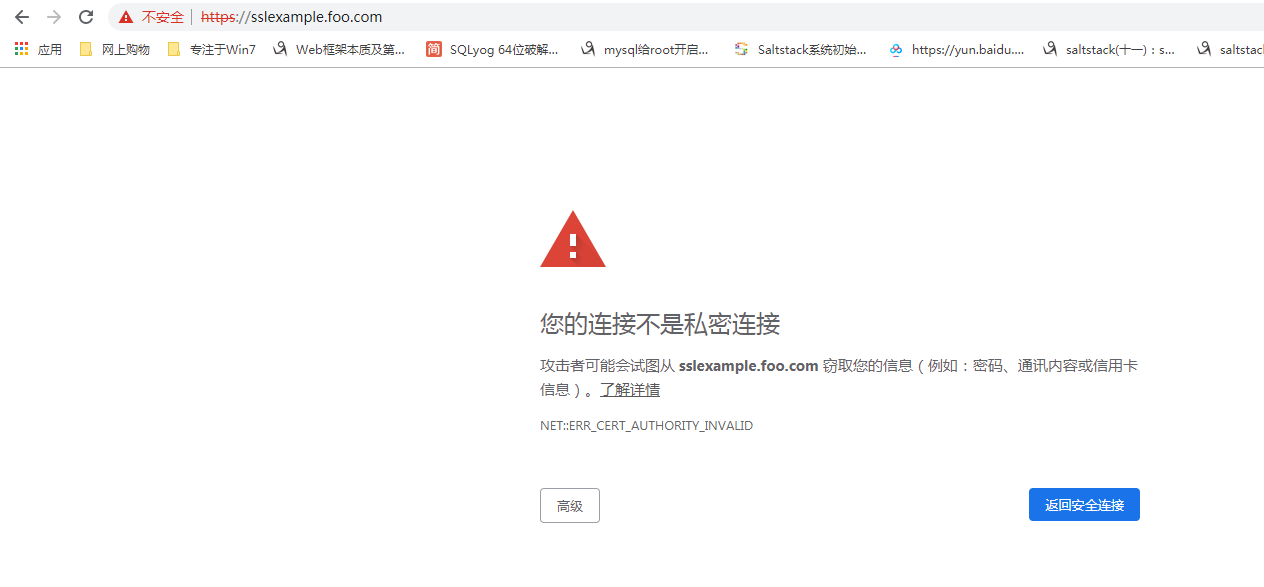
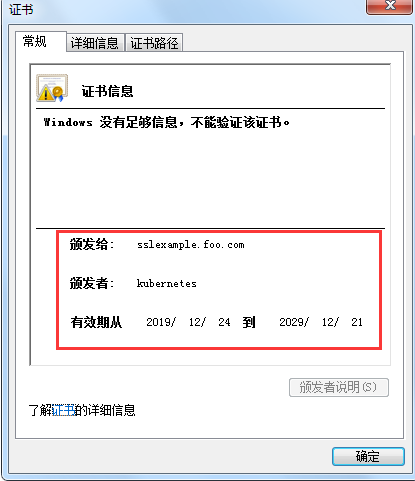
使用默认的 Ingress 证书
1 | # k8s 会默认自签证书 |
1 | # 启动 |
1 | # 测试 k8s自己颁发的证书 |
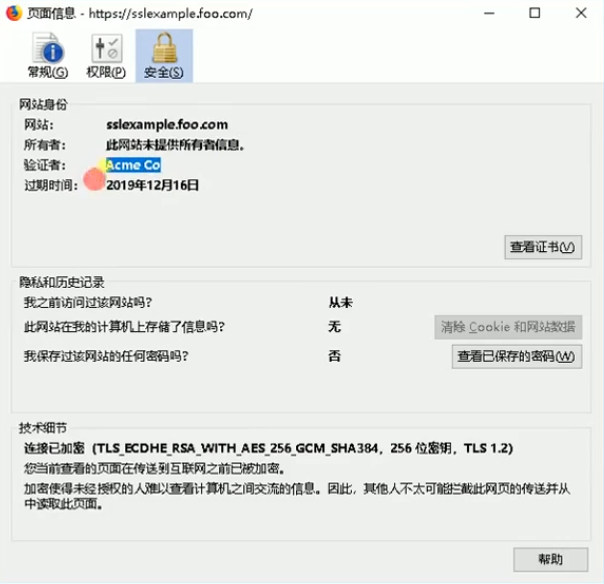
总结
- Ingress 支持 四层、七层负载均衡转发
- 支持自定义service访问策略
- 只支持基于域名的网站访问
- 支持TLS
- 用户 -> 域名 -> 负载均衡 -> 固定NODE的Ingress Controller(node) -> Pod\
- 部署多个 nginx-ingress-controller
- DaemonSet 方式部署到 多个指定标签的node节点上
